SOC 2 Type 2 Compliant Security

Create, share, and collaborate, knowing your data is safeguarded by the highest security standards.



4.7 out of 5 stars







Overview
Why
Types
Examples
Reviews
Tips
FAQ
Benchmark for Trust and Security
Creating projects that involve sensitive data often comes with challenges related to security, privacy, and compliance. Whether you’re working in marketing, journalism, or education, ensuring that the tools you use meet strict standards is crucial. That’s where Infogram’s SOC 2 Type 2 compliance comes in – it directly addresses these challenges by guaranteeing that your data is handled with the highest security standards.
SOC 2 Type 2 compliance is a critical benchmark for trust and security, especially in today’s world where data breaches are all too common. For Infogram users, this means you can create, share, and collaborate on visual projects with full confidence that your data is protected. Whether you're a content writer, data analyst, consultant, teacher, or student, knowing that Infogram meets this rigorous compliance gives you peace of mind.
With Infogram's SOC 2 Type 2 compliance, you don’t have to worry about security slowing you down. This allows professionals across various fields to focus on their work. Whether you're creating a marketing report, writing an engaging article, or developing a classroom project, you can feel assured that your data remains safe and secure.
Take advantage of Infogram's security standards today, and create with the confidence that your data is protected every step of the way!
If you want us to share a copy of the report, please contact us.
Why SOC 2 Compliance Matters
Learn about the benefits of SOC 2 compliance.

Strong Data Security
At Infogram, we understand that the security of your data is crucial. Protecting it from unauthorized access is at the heart of everything we do. That’s why we use a combination of industry-leading security measures such as firewalls and advanced intrusion detection systems.
Our intrusion detection systems monitor for any suspicious activity in real-time, allowing us to respond immediately to potential threats. By choosing Infogram, you can be confident that your data is always protected, so you can focus on your work without worrying about security breaches or unauthorized access to your information.

Guaranteed Reliable Availability
We know that your projects require constant access to the tools you need, which is why Infogram is designed to be available whenever you need it. Our platform is built with high availability in mind, ensuring that downtime is minimal, and you can access your data and tools 24/7.
We maintain rigorous operational standards to prevent interruptions and provide fast, reliable service even during peak usage times. You won’t need to worry about your workflow being disrupted due to outages. By prioritizing availability, we also make sure that performance and security remain high.

Accurate Data Processing
At Infogram, we go the extra mile to ensure that your data is processed with complete accuracy and reliability. We implement stringent quality assurance processes to ensure that every piece of information is handled correctly, without errors, delays, or data loss. Whether you’re processing data for analytics, visualization, or reporting, you can trust that it’s being done with precision and care.
Reliable data processing means that the results you get from our platform are trustworthy, allowing you to confidently make important business decisions. Our commitment to processing integrity gives you peace of mind that every data interaction is both accurate and efficient.

Protected Confidential Information
We take the confidentiality of your data seriously. Infogram uses cutting-edge encryption technology to protect your information during transmission and while it’s stored on our servers. This ensures that even if unauthorized parties attempt to intercept your data, they won’t be able to access it.
We also ensure that all confidential data is handled according to industry best practices, protecting it from accidental disclosure. With these measures, you can be confident that your confidential information remains private and secure at all times, allowing you to focus on your work with peace of mind.

Safeguarded Personal Privacy
Your privacy is essential to us at Infogram, and we’re dedicated to protecting it by adhering to stringent privacy policies and following all relevant data protection laws. We collect only the data necessary to provide our services and ensure it’s used responsibly, in accordance with clear and transparent privacy practices.
From secure data storage to handling user information appropriately, we go beyond just meeting the legal requirements. Our privacy measures are designed to protect your personal information from misuse or unauthorized sharing.
Explore Most Loved Features

Interactive Elements
Engage your audience with interactive elements such as tooltips, clickable legends, and drill-down functionality. Allow your stakeholders to explore the data in more detail and interact with the report for a deeper understanding.

Brand Kit
Ensure consistent branding across all your projects with a brand kit that allows you to upload and apply your brand's logos, color schemes, and fonts effortlessly.

Project Embeds
Integrate interactive visualizations directly into your website or blog, creating a more engaging and immersive experience for your audience.

Chart Library
Choose from a wide range of chart types, including bar charts, line graphs, pie charts, and more. Customize your charts with ease, adjusting colors, labels, and formatting to present your data in the most impactful way.

Data Import
Easily import data from Excel, Google Sheets, databases, and more. Infogram's seamless integrations and import capabilities make it effortless to bring your data into the reporting environment.

Annotations and Callouts
Enrich your reports with annotations and callouts to provide context and guide readers through the data. Add explanations, highlights, and insights to ensure your audience fully understands the information presented.

Customizable Templates
Infogram offers a collection of customizable templates designed specifically for reporting purposes. Start with a professionally designed template and tailor it to your needs, saving time and ensuring a polished look.
Get Inspired by Infogram User-Created Projects

10 Largest Mining-Focused Funds to Have Closed Historically

2024 ADF Annual Report
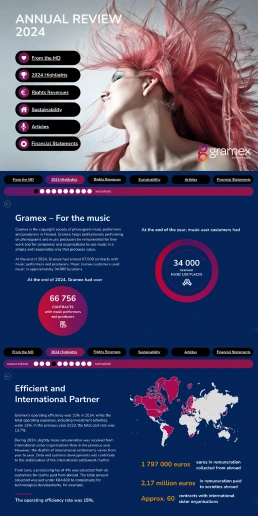
Annual Reviews

Deepwater Horizon Oil Spill

State of Digital Advertising

The Not Enough Impact Report 2018
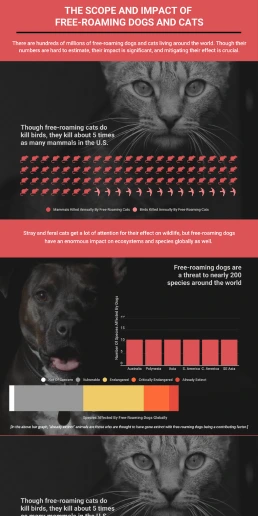
The Scope and Impact of Free-Roaming Dogs and Cats

Florida Seaports
Customer Reviews
Here is what our customers have to say about us.



2022 Summer & Fall and 2023 Winter leader in Data Visualisation Software 4.7 out of 5 stars
See reviews on G2 ›Empowering 30,000+ Companies Worldwide
From startups to established enterprises, our platform has been embraced by a diverse range of businesses seeking to captivate audiences and simplify complex data. Here are just a few examples of the 30,000+ companies that use Infogram.















Learn More Practical Tips
Business
Best Ways to Visualize and Analyze Polling Data
Data
AI for Data Analysis: Maximizing Value From Your Data
Data
The Complete Guide to Different Types of Charts
Design
20+ Graphic Design Tips for Mastering Your Visuals
Design
Chart Dos and Don’ts: The Ultimate Data Visualization Guide
Design
Good and Bad Data Visualization Examples
Frequently Asked Questions
What does SOC 2 Type II Certification mean?
SOC 2 Type 2 Certification is an auditing standard that shows how well a service provider, like Infogram, manages and protects customer data. It focuses on five key areas: security, availability, processing integrity, confidentiality, and privacy. This certification means we have been rigorously evaluated over time to ensure we meet these high standards.
How does Infogram meet SOC 2 Compliance Standards?
Infogram meets SOC 2 Compliance Standards by implementing strict security measures, regular monitoring, and continual improvements. We have processes in place to safeguard your data, ensure our services are consistently available, and maintain the confidentiality and privacy of your information.
How does SOC 2 Compliance Security help you succeed in professional and academic settings?
SOC 2 Security Compliance helps by providing peace of mind that your data is safe. This assurance allows you to focus on creating impactful projects without worrying about security risks. Whether you’re sharing sensitive information or collaborating with others, knowing your data is managed securely boosts your confidence and productivity.
Can I use Infogram for projects that involve sensitive data?
Yes! Infogram’s SOC 2 Type 2 Certification means we take data security seriously, so you can use our platform for projects that involve sensitive information with confidence. Just make sure to follow best practices for data sharing and privacy.
How often is Infogram evaluated for SOC 2 compliance?
Infogram undergoes regular evaluations to maintain our SOC 2 Type 2 Certification. This ongoing assessment helps us continuously improve our security measures and ensures we meet the high standards required to protect your data.
What are the main differences between SOC 2 Type 2 and ISO 27001?
Both SOC 2 Type 2 and ISO 27001 focus on information security. However, SOC 2 Type 2 is more specific to service organizations and how they manage customer data. ISO 27001 is a broader framework for establishing an information security management system (ISMS). Essentially, SOC 2 Type 2 is about the effectiveness of controls over time, while ISO 27001 is about having a comprehensive security management framework.
What are the main differences between SOC 2 Type 2 and GDPR?
Infogram complies with both SOC 2 Type 2 and GDPR (General Data Protection Regulation) by prioritizing data protection and privacy. We implement policies that ensure your personal data is handled securely and transparently. This means you can trust us to protect your information while using our platform.
What are the main differences between SOC 2 Type 2 and WCAG 2.2?
Infogram ensures compliance with SOC 2 Type 2 and WCAG 2.2 (Web Content Accessibility Guidelines) by designing our platform to be user-friendly and accessible to everyone, including those with disabilities. This commitment not only meets legal standards but also enhances the overall user experience, ensuring that all users can create projects effectively.
How can I learn more about Infogram's security policies?
What should I do if I have more questions about Infogram's security measures?
If you have further questions about our security measures or SOC 2 compliance, feel free to reach out to our support team. We're here to help you understand how we protect your data and ensure a secure experience on our platform.
Didn't find the answer? Check our FAQs

Try Infogram Now
Are you ready to unleash the power of data visualization? Get started with Infogram today and create stunning, interactive content that captivates your audience. Elevate your projects and bring data to life.
